Our cybersecurity software is here to provide you with the protection measures essential to your business. You don't need to invest in complex audits to ensure a first level of security that can thwart most attacks.
We take care of your security with our combination of top-notch security measures and cyber awareness program.
Show step by step how to get started.

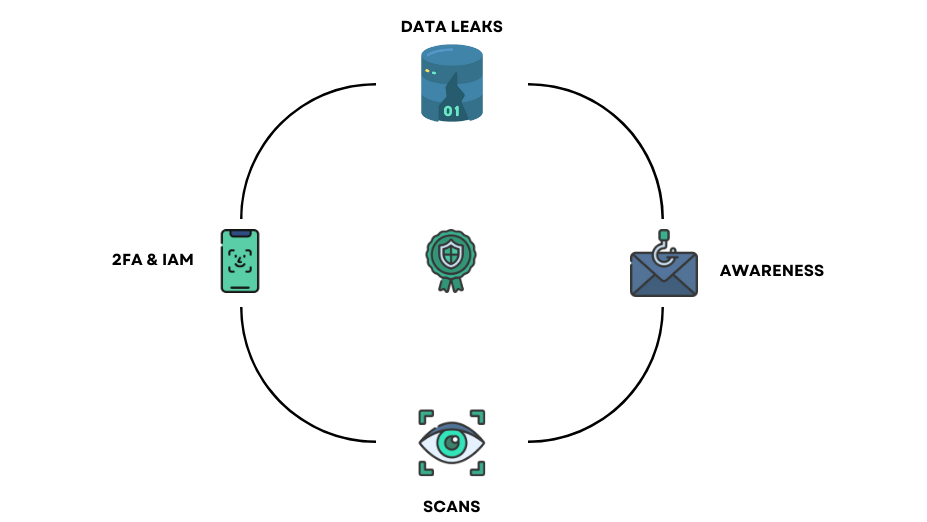
Our phishing campaign creation solution is an advanced cybersecurity tool that allows companies to test the resilience of their staff to phishing attacks. Phishing attacks are one of the most common and successful types of attacks used by cybercriminals to gain access to corporate computer systems.

When a data leak is detected, we immediately notify our customers so they can take the necessary steps to protect their sensitive data. We also provide detailed reports on detected data leaks and the steps taken to resolve them.

We offer customized vulnerability scans tailored to the specific needs of each company. We routinely scan external systems for potential vulnerabilities, such as web application security flaws, open ports, incorrect security configurations and more.

Our solution for verifying the presence of MFA on accounts and analyzing rights and privileges is an essential tool for ensuring the security of your company and its data. With this solution, we verify that MFA (multi-factor authentication) is enabled on all accounts in your organization and analyze the rights and privileges granted to each user.
Always know what you`ll Pay
Perfect for starters
If you have more tiers or lots of features, try the table.
See what your clients say about us
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa.
Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim.
In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium.
Contact us or sign up now.